Le phishing : une menace sous-estimée
La cybersécurité est un enjeu majeur pour les entreprises, et les campagnes de phishing malveillantes figurent parmi les menaces les plus fréquentes. Pourtant, les décideurs d’entreprises, y compris les CEOs et CTOs, sont parfois les maillons faibles en matière de sensibilisation.
Dans le cadre de sa mission de protection et de sensibilisation, Hackmosphere a mené une campagne de phishing ciblée auprès de ces profils stratégiques. Les résultats sont éloquents et soulignent la nécessité de renforcer la vigilance face aux e-mails malveillants.
Définition du phishing
Avant de plonger dans les détails de la recherche, il est important de comprendre ce qu’est réellement le phishing. Le phishing est une technique utilisée par les cybercriminels pour tromper les utilisateurs et obtenir des informations sensibles telles que des identifiants de connexion, des mots de passe ou des informations financières. Les attaquants utilisent des e-mails pour se faire passer pour une entité légitime, telle qu’une banque, une entreprise ou un service en ligne. Ils demandent ensuite aux victimes de divulguer leurs informations confidentielles en cliquant sur un lien malveillant ou en fournissant directement ces informations. Le phishing peut prendre différentes formes, notamment le spear-phishing qui cible spécifiquement une personne ou une organisation, et le whaling qui vise spécifiquement les cadres supérieurs d’une entreprise. Ces techniques sont souvent très sophistiquées et difficiles à détecter.

Approche et méthodologie de la campagne de phishing effectuée
Pour garantir la fiabilité des résultats, Hackmosphere a suivi une approche méthodique et rigoureuse.
Identification des cibles
La campagne visait deux types de décideurs clés :
- Les CEOs, souvent exposés en raison de leur rôle stratégique et de leurs interactions externes.
- Les CTOs, en charge des décisions technologiques et naturellement plus sensibilisés aux risques numériques.
Personnalisation des scénarios
Deux scénarios distincts ont été élaborés pour s’adresser spécifiquement à chaque cible :
- Un e-mail axé sur une demande de devis pour les CEOs, exploitant leur réactivité face aux opportunités commerciales.
- Une invitation à un sommet technologique pour les CTOs, jouant sur leur expertise et leur intérêt pour les événements professionnels.
Création de l’infrastructure & envoi des e-mails
Les e-mails ont été envoyés via une plateforme sécurisée et optimisés pour la délivrabilité. La méthode de création est un process assez complexe qui pourrait nécessiter un article de blog en soi. Ce process ne sera donc pas détaillé ici mais voici notre approche :
- Un nom de domaine a été acheté pour chaque scénario :
- meditech-innovation.fr pour les CEOs
- sommet-leaders-technologiques.fr pour les CTOs
- Nous avons créé notre propre infrastructure (Utilisation d’un VPS d’un cloud Privé. Installation d’outils tels que Postfix, Certbot ou Mailgun).
- Warmupinbox a ensuite été utilisé pour augmenter la crédibilité des adresses d’envoi et améliorer les taux de placement en boîte principale.
- Gophish a ensuite été utilisé pour créer les campagnes et suivre leur bon déroulement.
Récupération des résultats
Pour analyser les résultats, deux métriques ont été prises en compte :
- Les taux de clics
- Les performances des anti-spams utilisés par les volontaires
Exemple de timeline (heure de réception du mail et heure du clic par la victime) :

Limitations : vous pourriez vous demander pourquoi on n’est pas allé plus loin en demandant des informations confidentielles ? La raison est simple : Ayant des CEOs et CTOs volontaires et provenant de plusieurs horizons industriels, il a été difficile de trouver un scénario qui aurait été applicable à tous. Ainsi nous avons choisi de simplifier la campagne.
Quels sont les résultats de la campagne de phishing ?
Les CEOs : une cible vulnérable
L’e-mail envoyé aux CEOs simulait une demande de devis pour un appel d’offres. Il se présentait comme suit :
Objet : Devis pour une prestation
Message :
Bonjour,
Je vous contacte car j’ai identifié votre entreprise dans le cadre de ma recherche dans le domaine {{.Position}}. Je suis intéressé par ce que vous faites et aimerais obtenir un devis.
Si vous souhaitez participer à l'appel d'offre, merci de prendre rendez-vous dans mon agenda ici : {{.URL}}Résultats :
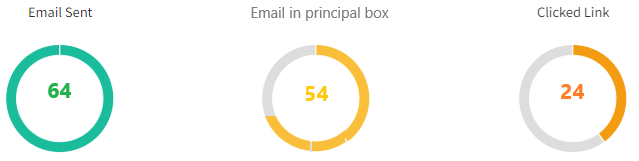
- 64 e-mails envoyés
- 54 e-mails arrivés dans la boîte principale (84.5 %)
- 24 clics sur le lien malveillant (37,5 %)
- Aucun clic depuis les e-mails arrivés en SPAM
Ces résultats montrent que près de 4 CEOs sur 10 se laissent piéger par une simulation réaliste, mettant en lumière leur exposition aux attaques par ingénierie sociale.
Les CTOs : une meilleure vigilance
L’e-mail destiné aux CTOs jouait sur leur expertise technique et leur intérêt pour les événements professionnels :
Objet : Invitation : Intervenez au Sommet des Leaders Technologiques 2025
Message :
Bonjour,
Nous serions heureux de vous accueillir parmi nos intervenants, pour partager vos idées sur l'avenir de l'innovation technologique dans le domaine {{.Position}}.
Si vous souhaitez en savoir davantage sur notre conférence, vous pouvez télécharger notre programme ici : {{.URL}}Résultats:
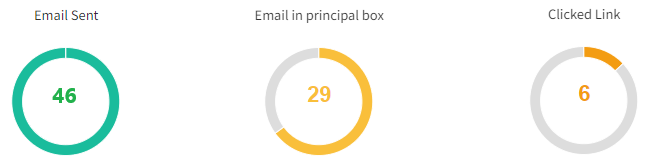
- 46 e-mails envoyés
- 29 e-mails arrivés dans la boîte principale (63 %)
- 6 clics sur le lien malveillant (13 %)
- Aucun clic depuis les e-mails arrivés en SPAM
Malgré une campagne crédible et ciblée, les CTOs se sont montrés globalement plus vigilants que les CEOs.
Analyse et enseignements clés
1. L’importance du facteur crédibilité
L’e-mail envoyé aux CEOs était plus crédible car il jouait sur un besoin professionnel concret (un devis pour une prestation), tandis que celui des CTOs reposait sur une promesse moins tangible (intervenir à un événement). Cela souligne l’importance de l’adaptation des attaques en fonction de la cible.
2. Les performances des systèmes anti-spam
Les statistiques révèlent une différence significative entre les filtres anti-spam des différents fournisseurs :
- Gmail : seuls 2 % des e-mails envoyés ont été placés en SPAM.
- Office 365 a quant-à-lui affiché la meilleure performance avec le meilleur taux de mise en SPAM.
3. L’entraînement des boîtes e-mails
L’e-mail destiné aux CEOs a bénéficié d’un meilleur entraînement (via warmupinbox), ce qui explique son meilleur taux de délivrabilité comparé à l’e-mail destiné aux CTOs. Ce détail technique montre l’importance des préparatifs dans la réussite des campagnes de phishing.
L’impact potentiellement catastrophique en cas de campagne de phishing réelle
Bien que cette campagne de phishing ait été conçue uniquement à des fins de sensibilisation, les résultats révèlent le risque immense auquel les entreprises s’exposent face à de véritables cybercriminels. Dans cette simulation, l’interaction s’arrêtait après le clic de la victime sur le lien malveillant. Cependant, dans une attaque réelle, ce clic aurait pu rediriger les victimes vers un site frauduleux conçu pour collecter des identifiants sensibles, installer des logiciels malveillants ou encore exfiltrer des données critiques.
Au-delà de l’impact immédiat associé à cette recherche, comme l’usurpation d’identité ou la compromission d’un système, les conséquences peuvent s’étendre à des niveaux stratégiques. Les entreprises peuvent subir des pertes financières importantes, des violations de données sensibles ou encore une atteinte grave à leur réputation. Ces scénarios soulignent l’urgence de renforcer les défenses contre le phishing, car une seule erreur humaine peut ouvrir la porte à une cyberattaque majeure.
Comment protéger votre entreprise contre les menaces liées au phishing ?
Les résultats de cette campagne doivent inciter les entreprises à renforcer leurs dispositifs de protection et de sensibilisation. Voici quelques recommandations clés :
- Former vos équipes régulièrement
Proposez des sessions de sensibilisation pour familiariser vos employés, y compris les décideurs, avec les techniques de phishing les plus courantes. - Renforcer vos systèmes de sécurité
Privilégiez des solutions robustes comme Office 365, qui s’est distingué dans cette campagne par son efficacité anti-spam. - Analyser les e-mails entrants avec vigilance
Encouragez une vérification systématique des expéditeurs et des liens (passer la souris sur les URL pour voir leur véritable destination) avant de cliquer. - Tester vos collaborateurs avec des campagnes internes
Organisez des simulations régulières pour évaluer le niveau de vigilance de vos équipes face aux e-mails malveillants.
Conclusion : la sensibilisation à la cybersécurité est un enjeu stratégique
Cette campagne de phishing, menée par Hackmosphere, a mis en lumière des vulnérabilités significatives chez les décideurs d’entreprise. Les CEOs, particulièrement exposés, doivent redoubler de vigilance, tandis que les CTOs montrent une meilleure résistance.
Pour protéger vos actifs numériques et renforcer la sécurité de votre organisation, une sensibilisation proactive et des outils performants sont essentiels.
Vous ne connaissez pas votre niveau de sensibilisation global ? Passez à l’action avec Hackmosphere
Vous souhaitez tester la vigilance de vos équipes ou renforcer votre cybersécurité ? Contactez-nous dès aujourd’hui pour découvrir comment Hackmosphere peut vous accompagner. Ensemble, construisons un environnement digital sûr et protégé.

